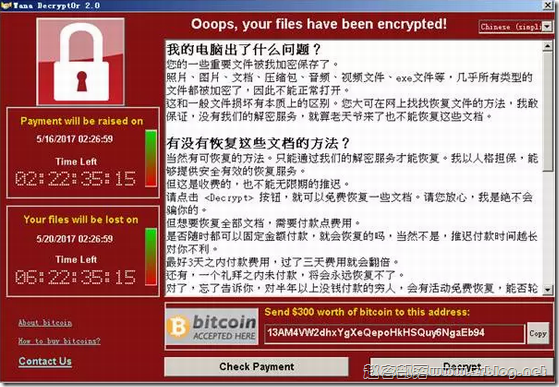
微软已发布了新的针对windows系统的漏洞补丁,请使用windows系统的读者留意该漏洞并及时处理避免对VPS及服务器使用造成不便。
Now that I have your attention, it is important that affected systems are patched as quickly as possible to prevent such a scenario from happening. In response, we are taking the unusual step of providing a security update for all customers to protect Windows platforms, including some out-of-support versions of Windows.
Vulnerable in-support systems include Windows 7, Windows Server 2008 R2, and Windows Server 2008. Downloads for in-support versions of Windows can be found in the Microsoft Security Update Guide. Customers who use an in-support version of Windows and have automatic updates enabled are automatically protected.
Out-of-support systems include Windows 2003 and Windows XP. If you are on an out-of-support version, the best way to address this vulnerability is to upgrade to the latest version of Windows. Even so, we are making fixes available for these out-of-support versions of Windows in KB4500705.
Customers running Windows 8 and Windows 10 are not affected by this vulnerability, and it is no coincidence that later versions of Windows are unaffected. Microsoft invests heavily in strengthening the security of its products, often through major architectural improvements that are not possible to backport to earlier versions of Windows.
There is partial mitigation on affected systems that have Network Level Authentication (NLA) enabled. The affected systems are mitigated against ‘wormable’ malware or advanced malware threats that could exploit the vulnerability, as NLA requires authentication before the vulnerability can be triggered. However, affected systems are still vulnerable to Remote Code Execution (RCE) exploitation if the attacker has valid credentials that can be used to successfully authenticate.
It is for these reasons that we strongly advise that all affected systems – irrespective of whether NLA is enabled or not – should be updated as soon as possible.
Resources
Links to downloads for Windows 7, Windows 2008 R2, and Windows 2008
Links to downloads for Windows 2003 and Windows XP
Simon Pope, Director of Incident Response, Microsoft Security Response Center (MSRC)
原文:https://blogs.technet.microsoft.com/msrc/2019/05/14/prevent-a-worm-by-updating-remote-desktop-services-cve-2019-0708/
百度翻译:
通过更新远程桌面服务(CVE-2019-0708)防止蠕虫病毒 ★★★★★★★★★★★★★★★★★★ MSRC团队化身MSRC团队20190年5月14日 今天,微软发布了对远程桌面服务(以前称为终端服务)中影响某些旧版本Windows的关键远程代码执行漏洞CVE-2019-0708的修复。远程桌面协议(RDP)本身不易受攻击。此漏洞是预身份验证,不需要用户交互。换句话说,该漏洞是“可恶的”,这意味着任何利用该漏洞的未来恶意软件都可能以类似于2017年在全球传播的Wannacry恶意软件的方式从易受攻击的计算机传播到易受攻击的计算机。虽然我们没有发现对该漏洞的利用,但恶意参与者很可能会针对该漏洞编写一个漏洞并将其合并到恶意软件中。 现在我得到你们的注意,重要的是尽快修补受影响的系统,以防止这种情况发生。作为回应,我们采取了不同寻常的步骤,为所有客户提供安全更新,以保护Windows平台,包括一些不支持的Windows版本。 支持系统中的漏洞包括Windows 7、Windows Server 2008 R2和Windows Server 2008。有关Windows支持版本的下载,请参阅《Microsoft安全更新指南》。使用支持中版本的Windows并启用自动更新的客户将被自动保护。 不支持的系统包括Windows 2003和Windows XP。如果您的版本不受支持,解决此漏洞的最佳方法是升级到最新版本的Windows。即便如此,我们仍在为KB4500705中不支持的Windows版本提供修复程序。 运行Windows 8和Windows 10的客户不受此漏洞的影响,而且Windows的较新版本不受影响也不是巧合。微软投入巨资加强其产品的安全性,通常是通过主要的体系结构改进,而这些改进不可能回到早期版本的Windows。 对启用了网络级身份验证(NLA)的受影响系统进行了部分缓解。由于NLA在触发漏洞之前需要身份验证,因此受影响的系统可以抵御可能利用该漏洞的“易受攻击”恶意软件或高级恶意软件威胁。但是,如果攻击者具有可用于成功进行身份验证的有效凭据,则受影响的系统仍然容易受到远程代码执行(RCE)攻击。 出于这些原因,我们强烈建议尽快更新所有受影响的系统,无论NLA是否启用。
 个人生活记录
个人生活记录